Decentralized Identity (DID) – A Comprehensive Overview
The concept of Decentralized Identity (DID) is gaining momentum in the blockchain and digital identity space. In a world where data breaches, identity theft, and privacy concerns are ever-growing, DID offers a new paradigm that aims to give individuals control over their identity without relying on centralized authorities like governments or tech companies. This system empowers users to manage, verify, and share their identity securely and privately.
This article will explore what Decentralized Identity (DID) is, how it works, its benefits, key components, and use cases in the evolving digital landscape.
1. What is Decentralized Identity (DID)?
A Decentralized Identity (DID) is a new type of digital identity that is not controlled by a central authority such as a government, social media platform, or financial institution. Instead, DIDs are managed on a decentralized blockchain network, allowing individuals to own and control their personal data. This type of identity system uses public-key cryptography to ensure that users can authenticate themselves and prove their identity without relying on traditional intermediaries.
Key Characteristics of DID:
- Self-sovereign: The user fully owns and controls their identity.
- Verifiable: Information about the identity is verifiable using cryptographic signatures, ensuring authenticity.
- Portable: DIDs can be used across different platforms and services.
- Privacy-focused: Data is shared only when necessary, and the user has full control over who gets to see it.
2. How Does Decentralized Identity (DID) Work?
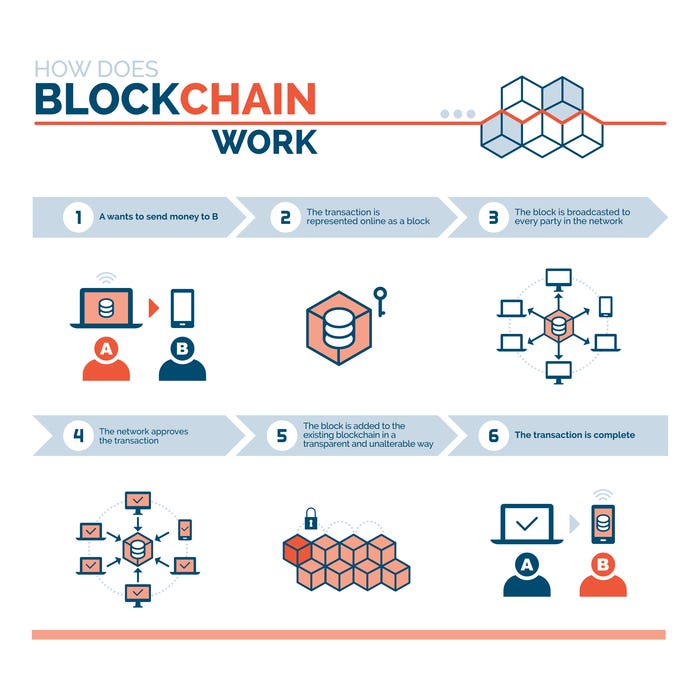
DIDs rely on blockchain technology and cryptographic principles to create an identity system that operates without central oversight. Below are the steps involved in how a DID works:
a. Creation of a DID
- A user generates a DID using a decentralized system, typically on a blockchain. The DID is associated with a public-private key pair.
- The private key remains with the user, ensuring that they can prove ownership and control over the DID without exposing sensitive data.
- The public key can be shared with others for verification, but no personal data is included in the DID itself.
b. Decentralized Identifiers (DIDs) and DID Documents
- A DID is associated with a DID document, which contains critical information about the DID.
- The DID document includes metadata such as authentication methods, verification methods, and public keys for communication.
- This document is stored on a blockchain or other decentralized network, making it immutable and resistant to tampering.
c. Authentication and Verification
- To authenticate their identity, the user signs transactions using their private key. This signature can then be verified by others using the associated public key.
- When interacting with a service or platform, the user can share their DID and, if needed, a proof of identity.
- The service can check the authenticity of the DID using blockchain-based verification, ensuring that the identity is not manipulated or forged.
d. Decentralized Identity Trust Frameworks
- Trust frameworks are used to establish how DID-related data is managed, verified, and shared. These frameworks define the rules for how identity data can be used in various contexts, whether for authentication, age verification, or credential issuance.
3. Key Components of Decentralized Identity (DID)
To understand how DID functions, it’s essential to explore the key components that make up the system:
a. DIDs (Decentralized Identifiers)
- DID is the identifier that represents a person, organization, or thing in a decentralized manner.
- A DID is not bound to a central authority, and it can be used across various platforms for identification purposes.
b. DID Documents
- A DID document is a file that holds the associated metadata for the DID. It contains important details like:
- Public keys for authentication and verification.
- Service endpoints (e.g., URLs to interact with applications).
- Methods to prove ownership and control.
c. Verifiable Credentials (VCs)
- Verifiable Credentials (VCs) are digital statements that can be issued to users. These credentials are cryptographically signed by a trusted issuer (such as a university, employer, or government).
- VCs are used to prove identity attributes such as age, education, or professional certifications.
- These credentials can be shared selectively, allowing users to prove specific aspects of their identity without revealing all their personal information.
d. Decentralized Identifiers (DID Methods)
- The DID methods define how the DID is created, resolved, and managed. Examples of DID methods include Bitcoin-based DIDs, Ethereum-based DIDs, or even IPFS-based DIDs.
- Each DID method determines the way data is stored on the blockchain and the level of privacy provided by the system.
e. Blockchain or Distributed Ledger Technology (DLT)
- Blockchain or DLT is used to store the DID documents, ensuring the integrity and security of identity-related information.
- The decentralized nature of the blockchain ensures that identity data cannot be tampered with by a single entity, making it more secure and resistant to hacking.
4. Benefits of Decentralized Identity (DID)
DID systems offer several advantages over traditional identity management systems:
a. User Control and Ownership
- With DID, users own and control their own identity, including the data associated with it. No third-party can control, modify, or steal this data without the user’s consent.
b. Enhanced Privacy and Security
- DIDs do not require users to share excessive amounts of personal information. The user can prove their identity without revealing unnecessary details.
- The system uses cryptographic proofs to authenticate identity, reducing the risks of data breaches and identity theft.
c. Reduced Dependency on Centralized Authorities
- Users are no longer reliant on centralized organizations like government agencies, banks, or social media platforms for identity management. This reduces the potential for discrimination, censorship, and fraud.
d. Interoperability
- DIDs are designed to be used across different platforms and services. This means that a single decentralized identity can be used to log into various websites, sign contracts, or verify credentials without creating multiple accounts.
e. Immutable and Tamper-Proof
- Since DIDs are stored on the blockchain, they are immutable. Once created, they cannot be changed, ensuring that identity data remains secure and accurate over time.
f. Cost-Effective
- Traditional identity management systems often involve high costs due to third-party verification, administrative overhead, and paper-based procedures. DIDs eliminate these costs, making identity management more cost-effective.
5. Use Cases for Decentralized Identity (DID)
a. Digital Identity Verification
- DID can be used for secure online authentication, allowing users to prove their identity on various platforms without relying on usernames and passwords.
b. Access Control and Permissions
- DIDs can be used to manage access to physical and digital assets. For instance, users could authenticate to buildings, devices, or cloud services using their decentralized identity.
c. Voting and Governance
- In decentralized governance systems or DAO (Decentralized Autonomous Organizations), DIDs can be used to prove eligibility to vote or participate in decision-making.
d. Healthcare
- DIDs can be used to store and share healthcare credentials, such as vaccination status or medical records, enabling patients to share their health data securely with healthcare providers.
e. Credential Issuance and Management
- Educational institutions, employers, and government agencies can issue verifiable credentials (VCs) to individuals, ensuring that the information is accurate and verifiable without relying on centralized databases.
6. Challenges of Decentralized Identity (DID)
Despite its numerous benefits, DID faces several challenges:
a. Adoption and Interoperability
- Widespread adoption of DID systems requires standardization and interoperability between different platforms, blockchains, and services.
b. Regulatory and Legal Frameworks
- Governments and regulatory bodies may struggle to define and implement regulations around decentralized identity management, including privacy concerns and compliance.
c. Scalability
- As DID systems grow, the underlying blockchain infrastructure must scale efficiently to handle increasing numbers of identities and transactions.
d. Usability
- To ensure mass adoption, DID systems need to be user-friendly and accessible to individuals with limited technical knowledge.
7. Conclusion
Decentralized Identity (DID) is a revolutionary approach to identity management that offers individuals more control, privacy, and security. By leveraging blockchain technology, DIDs allow users to create, store, and manage their identity data in a decentralized and tamper-proof manner.
As the technology matures, we can expect to see increased adoption across industries such as finance, healthcare, education, and governance. However, challenges related to interoperability, scalability, and regulatory frameworks must be addressed for DID systems to achieve widespread use.
In a world where personal data is becoming increasingly valuable and vulnerable, DID represents a crucial step forward in empowering individuals to take control of their digital identity.